Как бросить курить и обойтись без чувства лишения методы снижения тяги к сигаретам
Подготовка к броску курения Как бросить курить и при этом избежать чувства лишения? Ответ на этот вопрос начинается с подготовки к важному шагу — броску курения. Это первый и решающий этап в пути к никотиновой независимости. Прежде всего, установите дату, с которой вы намерены окончательно прекратить курение. Эта дата станет вашим точным планом и мотивацией…
Психологическая поддержка при отказе от курения: как она работает
Понимание никотиновой зависимости Никотиновая зависимость — сложное и многогранное явление, которое требует глубокого понимания для успешного преодоления. Это состояние возникает в результате долгосрочного и регулярного употребления никотина, сильно ассоциированного с курением табака. Для полного осознания этой зависимости важно учитывать как физиологические, так и психологические аспекты. С физиологической точки зрения, никотин воздействует на мозг, взаимодействуя с…
Мифы и реальность никотиновой зависимости: разбираемся вместе
Миф #1: «Курение – всего лишь привычка» Курение долгое время рассматривалось как обычная привычка, которую можно легко побороть. Однако такой взгляд далек от истины. Курение — это гораздо более сложное явление, чем простая повседневная привычка. Оно основано на химической зависимости от никотина, а это вещество, входящее в состав табачного дыма, обладает мощным воздействием на мозг…
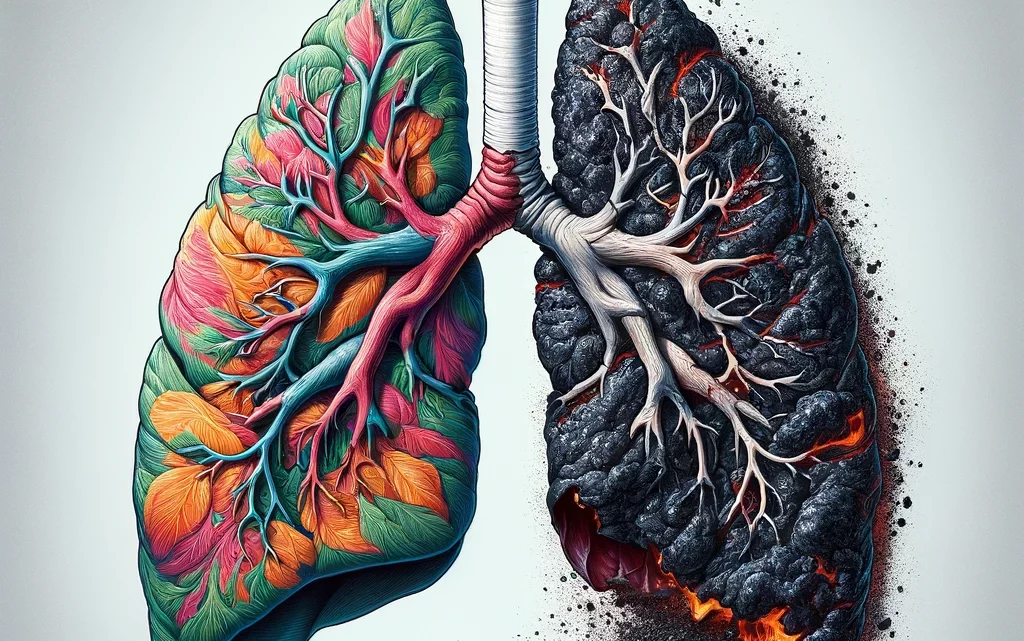
Влияние курения на здоровье: от сердца до легких
Воздействие на сердечно-сосудистую систему Курение оказывает немедленное деструктивное воздействие на сердечно-сосудистую систему, увеличивая риск развития серьезных заболеваний, таких как коронарная болезнь сердца, атеросклероз и периферическое артериальное заболевание. Никотин и другие токсичные вещества, содержащиеся в сигаретном дыме, стимулируют выработку адреналина, что приводит к повышению артериального давления и частоты сердечных сокращений, создавая дополнительную нагрузку на сердце. Долгосрочное…
Скрытые угрозы курения: что вам не рассказывают производители
Скрытые химические вещества в сигаретах Сигаретный дым содержит тысячи химических соединений, многие из которых вредны для здоровья, но не все они широко известны общественности. Производители табачных изделий часто умалчивают о полном составе своей продукции, оставляя курильщиков в неведении о потенциальных рисках. Эти вещества включают канцерогены, токсины, и даже радиоактивные элементы, которые могут вызывать различные заболевания,…
Десять проверенных стратегий избавления от сигаретной зависимости
Понимание своей зависимости Каждый курильщик уникален, и путь к освобождению от зависимости начинается с глубокого самопознания. Важно осознать, что курение — это не просто физическая потребность, но и психологическая привычка. Многие курильщики достигают точки, когда сигарета становится ответом на стресс, способом расслабления или средством для поддержания социальных связей. Разбирательство в своих привычках и триггерах, которые…